North Korea’s illicit cyber activity has grown increasingly sophisticated under Kim Jong-un’s rule. Kim views cyber warfare capabilities as an “all-purpose sword” that can fuel North Korean military asymmetrical capabilities such as nuclear weapons and missiles. Prominent cyberattack cases include the 2014 Sony Pictures hack, the 2016 Bangladesh Bank heist, and the 2017 WannaCry attack.
North Korea has intensified carrying out cyberattacks on financial institutions, cryptocurrency, and Decentralized Finance sectors as a means of generating illicit revenue streams. Cryptocurrency and North Korea may seem like an unlikely pairing as North Korea is perceived as a country disconnected from advanced technology and finance. In reality, North Korea has been deeply engaged in extralegal cryptocurrency activities including hacking, stealing virtual assets, and money laundering, which have become important tools of North Korea’s illicit financing. Since 2017, North Korea has increased attempts to hack the crypto industry to diversify its fund acquisition methods.
North Korea is becoming adept at using cryptocurrency to evade sanctions. In late 2017, North Korean hackers attacked South Korean and Japanese cryptocurrency exchanges coinciding with the soaring Bitcoin price. The international community imposed severe sanctions in this period after North Korea’s nuclear test in September 2017, and North Korean crypto heist operations intensified as a new sanction regime constrained North Korea’s ability to generate revenue, leading them to diversify their income stream without sanctions restrictions. In addition, North Korea’s self-quarantine from the outside world due to COVID-19 made it difficult to acquire foreign funds. However, North Korea increased its cryptocurrency hacking attempts with a significant amount of stolen funds, marking a record-high $1.7 bln in 2022. This recent increase indicates that cryptojacking is crucial for revenue generation and can
According to an FBI advisory, North Korea is actively stealing cryptocurrency and hacking DeFi. It is a concerning issue not only for the United States and its allies but also for every other country because such activities not only damage companies and individuals but also help fund North Korea’s weapons of mass destruction (WMD) and missile program, blurring the line between traditional and non-traditional security threats.
Linkage to Missile Tests?
The increasing number of hacks shows North Korea’s growing interest and attempts in cryptojacking. The graph below shows an increase in cryptocurrency theft starting around 2016 with a sharp hike in 2018 and 2022. It shows a similar trend between the value of stolen cryptocurrencies (orange) and the number of launches (blue). An Increase in hacking attempts (red) and total cryptocurrency value stolen may be caused by the strong international sanctions imposed in 2017. The 2022 figure is likely attributed to the border closure due to the COVID-19 pandemic, as North Korea sought to secure funds through cyberattacks in the absence of external trade.
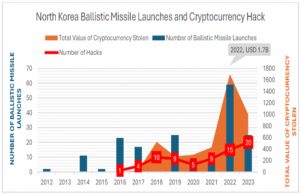
Data collected from Chainalysis and Japan Ministry of Defense and visualized by the author.
While limited access to information pertaining to North Korea’s resource allocation makes it difficult to establish a causal relationship, successful cryptocurrency hacks are correlated with increases in North Korea’s budget for numerous missile tests. Research suggests that Kim likely uses funds acquired by North Korean hackers to fund its ballistic missile programs. North Korea-related hacking groups such as Lazarus Group, Kimsuki, and Andariel operate under the Reconnaissance General Bureau of the Korea People’s Army (KPA). North Korea’s cyber operations are heavily supported by the Kim regime, and generated revenues are certainly utilized directly by the KPA. For example, the Kim regime actively nurtures North Korean students who perform well in math and computer science and recruit them into these hacking groups. The White House speculates that 50% of North Korea’s foreign currency acquisition comes from cyber theft, and institutions and experts evaluate the threat of North Korea’s cryptocurrency operation is growing year by year. Thus, funds acquired by highly systemized state-led crypto heists are likely to support the Kim regime and the national objective of WMD/missile development.
How Does North Korea Utilize Cryptocurrency to Acquire Funds?
According to the Harvard Belfer Center, North Korea uses three methods for acquiring funds via crypto operation: mining, initial coin offering (ICO), and cryptojacking. Cryptocurrency can be mined by solving complicated mathematical problems and this method is not a violation of international law. However, mining requires a lot of electricity and time, which is inefficient for North Korea due to its lack of electricity.
ICO is the process through which companies in the blockchain and cryptocurrency space raise capital to launch new tokens, apps, goods, or services. It is a similar term to Initial Public Offerings (IPOs), in which a company seeks investment from the public by exchanging shares. There has been only one fraudulent ICO case that turned out to be North Korea’s attribution (Marine Chain) in 2018 so far.
Last and most importantly, North Korea is deeply involved in cryptojacking: cryptocurrency hijacking followed by a laundering process called “mixing” and cashing out. The threat level of cryptojacking is the highest among the three methods, leading to significant amounts stolen, increasing number of attempts, and widespread impact across individuals and industries. Moreover, cryptojacking effectively evades international sanctions such as the United Nations Security Council (UNSC) and US sanctions as the nature of cryptocurrency and DeFi, in which financial intermediary institutions are not necessary for transacting cryptocurrencies, provides North Korea fewer obstacles because there are not as many regulations and countermeasures as traditional financial institutions. North Korea takes advantage of this gap to acquire funds that can help support the Kim regime and WMD/missile programs.
Why Cryptocurrency/DeFi?
North Korea hacks cryptocurrency and DeFi systems for economic gains with fewer barriers than traditional financial institutions. Lessons from the 2016 Bangladesh Bank heist showed North Korean hackers limitations of hacking traditional financial institutions as they only could acquire $100 mln (USD) out of attempted $1 bln due to systemic factors such as business hours and time difference that hindered North Korea’s attempt in transferring money from Bangladesh to Philippines. However, unlike conventional banks, cryptocurrency and DeFi platforms have minimal transactional constraints, regulatory oversight, and weaker security, allowing North Korean hackers to exploit vulnerabilities with less risk.
The inconsistency in the financial regulatory landscape for cryptocurrency, enables North Korean hackers to operate in regions with weak protections and evade coordinated enforcement efforts, making it an ideal environment for cyber theft. Moreover, DeFi networks offer sophisticated methods to obscure funds’ origins, with techniques like “mixers” and “tumblers” making it difficult to trace transactions back to North Korea. The decentralized nature creates further gaps in security, giving North Korea easier access to funds to support its regime despite international sanctions.
Challenges to Sanctions
The challenges of countering North Korea’s cryptocurrency hacking are deeply rooted in a lack of global cooperation in sanctioning North Korea’s crypto activity. Despite the existence of global cryptocurrency governance mechanisms, those do not have enforcing power to counter North Korea’s illicit crypto heist. Without unified international sanctions, North Korean crypto operations pose threats to the global community, remaining vulnerable to cryptojacking. While some countries have attempted to impose unilateral sanctions, such as the U.S. targeting North Korean cybercrime, but absence of international compliance makes these measures largely ineffective as the decentralization and transnationality of cryptocurrency and DeFi complicates enforcement, which gives North Korean hackers the ability to circumvent obstacles. North Korea will always find a place with access to cryptocurrency and shift hacking operations, for example, emerging crypto markets such as Central and South Asia.
Geopolitical rivalries have hindered efforts to expand sanctions through the UNSC, particularly because of Russia and China. For example, the expiration of the UN Panel of Experts on North Korea sanctions, following Russia’s veto and China’s abstention, highlights the lack of consensus on addressing North Korea issues. Furthermore, UNSC sanctions currently lack provisions specifically targeting cryptocurrency hacking, leaving a significant gap in the international response. As a result, North Korea continues to exploit this gap with relative impunity, undermining global sanctions efforts and effectively funding its nuclear and missile programs. Without coordinated, binding international action, North Korea’s cyber operations will likely continue to challenge global security.
Recommendations
Despite growing threats, the lack of international coordination prevents meaningful action to address North Korea’s cryptojacking. However, realistic approaches to global cooperation to address this problem exist. First, the US and like-minded countries should consider closer cooperation with Southeast Asian countries. Southeast Asia is particularly significant as North Korea has increased its cyber operations, Southeast Asian countries are experiencing North Korea’s cyberattacks, including the 2016 Bangladesh Bank hack, which is likely to share interest among them in countering Pyongyang’s illicit cyber operations.
Considering these factors, the US should take the lead in creating a Joint Cyber Cooperation Working Group (CCWG) with like-minded countries for cybersecurity cooperation with Southeast Asia by enhancing Southeast Asian countries’ cybersecurity capabilities. to enhance joint countermeasures against North Korea’s cyber activities, especially targeting the cryptocurrency industry. Also, as the EU and South Korea share their interest in building cybersecurity capacity for third countries according to their Digital Partnership, the US can connect these two regions with Southeast Asia for further interconnected cooperation on countering North Korea’s crypto operations in Southeast Asia. Furthermore, the US is also working with ASEAN regarding cyber security with the US-ASEAN Cyber Policy Dialogue.
Taking advantage of this unique position, the US can aim to build an interconnected cyber network by linking Europe, Northeast Asia, and Southeast Asia. All regions share the same threat from North Korea’s crypto heists, thus, there is a diplomatic opportunity to converge these interests into one by creating a US-led Joint CCWG.
Second, strengthening the international sanctions on North Korea’s illicit cyber activity is another option. However, as mentioned above, the UNSC is limited in drawing any agreements on North Korea issues. Recent research by the Center for Strategic and International Studies suggests that the G7 could serve as an alternative international framework given the current inefficacy of the UNSC and other international governance. Applying this approach, the G7 can become an actionable international coalition by implementing sanctions and encouraging other states to join to counter North Korea’s international cryptojacking threat. The De-Fi platform hack is difficult to prevent without coordinated regulations and countermeasures followed by robust implementation by all countries. However, considering the ineffectiveness of the UNSC on North Korea issues, utilizing existing multilateral frames currently remains a more realistic option for strengthening sanctions. As the US, South Korea, and Japan recently launched an alternative North Korea sanctions monitoring mechanism, an alternative sanctions regime through other mini/multilateral frameworks is another option.
In addition, public-private cooperation is crucial. The cryptocurrency issue is not well-spotlighted within politics, scholars, and experts. To fill this gap of understanding between cryptocurrency and North Korea policy, there should be active public-private cooperation and discussions between experts in two distinct areas to bridge the knowledge gap and facilitate active cooperation.
Lastly, the US and like-minded countries can actively lead different countermeasures, for example, publicizing information for spreading awareness of North Korea’s hacking, public-private cooperation on cryptocurrency and blockchain technology, and researching with the intelligence community. Although cooperation with China on the North Korea issue is difficult, Beijing’s crackdowns on cryptocurrency indicate its interest in financial stability and eradicating money laundering. Also, current North Korea-China relations seem to be dwindling as the growing ties between North Korea and Russia go against Beijing’s interests. As North Korean hackers are trained and conduct crypto operations in China, the US and its allies should discuss with Beijing regarding surveillance of these illicit activities. Here, the US and like-minded countries can try to put a wedge between China and North Korea through the art of diplomacy.
Hyunseung Yu is a master’s student at Georgetown University’s Walsh School of Foreign Service Asian Studies Program. His research focuses on Northeast Asian security issues mainly on the Korean Peninsula, such as inter-Korean security issues, US alliance relations in East Asia, and nuclear weapons. He is currently an intern at the Wilson Center’s Hyundai Motor-Korea Foundation Center for Korean History and Public Policy and a Research Assistant at Georgetown University Center for Security Studies.
Disclaimer: All opinions in this article are solely those of the author and do not represent any organization.
Photo: A North Korean flag is shown as the backdrop to images of Bitcoin and missiles. Source: Julia Dufossé